HTTPS 호출에 대한 TLS 설정 확인하는 방법
재미있는 글이 올라왔습니다. ^^
Docker를 이용한 TLS 테스트 방법에 대하여
; http://www.csharpstudy.com/DevNote/Article/30
openssl에 이런 기능이 다 있었군요. ^^ 이걸 보니 저도 예전에 TLS 버전에 따른 통신이 제대로 동작하는지 네트워크 모니터 도구를 이용해 확인한 글이 떠오릅니다.
TLS 1.2를 적용한 IIS 웹 사이트 구성
; https://www.sysnet.pe.kr/2/0/1834
(개인적으로, 이렇게 확인할 수 있는 방법에 대해 아는 것을 개발자로써도 중요하다고 생각합니다.)
미리 말씀드리면 이 글은, 단순히
Docker를 이용한 TLS 테스트 방법에 대하여 내용에 대한 복사 글입니다. 대신 위의 글에서는 linux가 담긴 docker 이미지를 이용하지만 윈도우 10의 경우 단순히 "Ubuntu" store app으로도 간단하게 해볼 수 있습니다.
Ubuntu
; https://www.microsoft.com/en-us/store/p/ubuntu/9nblggh4msv6
그리하여 repository 업데이트해주고,
$ sudo apt-get update
[sudo] password for testuser:
Hit:1 http://archive.ubuntu.com/ubuntu xenial InRelease
Get:2 http://archive.ubuntu.com/ubuntu xenial-updates InRelease [102 kB]
Get:3 http://archive.ubuntu.com/ubuntu xenial-backports InRelease [102 kB]
Get:4 https://packages.microsoft.com/repos/microsoft-ubuntu-xenial-prod xenial InRelease [2,846 B]
...[생략]...
Get:19 http://security.ubuntu.com/ubuntu xenial-security/restricted amd64 Packages [7,224 B]
Get:20 http://security.ubuntu.com/ubuntu xenial-security/restricted Translation-en [2,152 B]
Get:21 http://security.ubuntu.com/ubuntu xenial-security/universe amd64 Packages [322 kB]
Get:22 http://security.ubuntu.com/ubuntu xenial-security/universe Translation-en [121 kB]
Get:23 http://security.ubuntu.com/ubuntu xenial-security/multiverse amd64 Packages [3,208 B]
Fetched 3,383 kB in 23s (141 kB/s)
Reading package lists... Done
openssl 설치 후,
$ sudo apt-get install openssl
Reading package lists... Done
Building dependency tree
Reading state information... Done
The following packages will be upgraded:
openssl
1 upgraded, 0 newly installed, 0 to remove and 112 not upgraded.
Need to get 492 kB of archives.
After this operation, 0 B of additional disk space will be used.
Get:1 http://archive.ubuntu.com/ubuntu xenial-updates/main amd64 openssl amd64 1.0.2g-1ubuntu4.10 [492 kB]
Fetched 492 kB in 60s (8,167 B/s)
(Reading database ... 33004 files and directories currently installed.)
Preparing to unpack .../openssl_1.0.2g-1ubuntu4.10_amd64.deb ...
Unpacking openssl (1.0.2g-1ubuntu4.10) over (1.0.2g-1ubuntu4.9) ...
Processing triggers for man-db (2.7.5-1) ...
Setting up openssl (1.0.2g-1ubuntu4.10) ...
SSL 통신을 위한 인증서를 만들고,
$ openssl req -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 3650 -nodes
Generating a 4096 bit RSA private key
.............++
.............................++
writing new private key to 'key.pem'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:.
State or Province Name (full name) [Some-State]:.
Locality Name (eg, city) []:.
Organization Name (eg, company) [Internet Widgits Pty Ltd]:.
Organizational Unit Name (eg, section) []:.
Common Name (e.g. server FQDN or YOUR name) []:localubuntu
Email Address []:.
생성된 인증서 파일을 기반으로,
$ ls
cert.pem key.pem
https 요청을 받을 수 있도록 서비스를 개시합니다.
$ openssl s_server -key key.pem -cert cert.pem -accept 44300 -www
Using default temp DH parameters
ACCEPT
140449884276376:error:1407609C:SSL routines:SSL23_GET_CLIENT_HELLO:http request:s23_srvr.c:394:
ACCEPT
140449884276376:error:1407609C:SSL routines:SSL23_GET_CLIENT_HELLO:http request:s23_srvr.c:394:
ACCEPT
140449884276376:error:1407609C:SSL routines:SSL23_GET_CLIENT_HELLO:http request:s23_srvr.c:394:
...[생략]...
인증서 만드는 과정에서 FQDN을 localubuntu로 했기 때문에 HOSTS 파일에 다음과 같이 이름을 하나 등록해 줍니다. (어차피 유효하지 않은 인증서라 사실 등록할 필요가 없습니다.)
127.0.0.1 localubuntu
이제 웹 브라우저를 이용해 "https://localubuntu:44300" 주소로 방문하면, 다음과 같이 신뢰할 수 없는 인증서라고 나옵니다.
어차피 테스트이니, 그냥 "Go on to the webpage (not recommended)" 링크를 눌러 진행하면 다음과 같이 상세한 SSL/TLS 설정 상황을 확인할 수 있습니다.
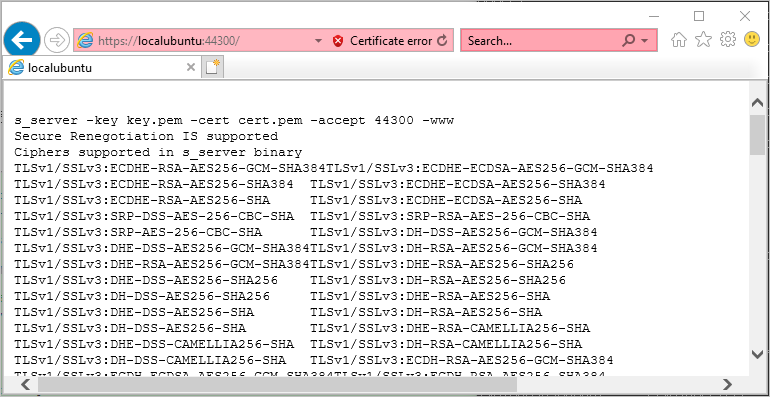
s_server -key key.pem -cert cert.pem -accept 44300 -www
Secure Renegotiation IS supported
Ciphers supported in s_server binary
TLSv1/SSLv3:ECDHE-RSA-AES256-GCM-SHA384TLSv1/SSLv3:ECDHE-ECDSA-AES256-GCM-SHA384
TLSv1/SSLv3:ECDHE-RSA-AES256-SHA384 TLSv1/SSLv3:ECDHE-ECDSA-AES256-SHA384
TLSv1/SSLv3:ECDHE-RSA-AES256-SHA TLSv1/SSLv3:ECDHE-ECDSA-AES256-SHA
TLSv1/SSLv3:SRP-DSS-AES-256-CBC-SHA TLSv1/SSLv3:SRP-RSA-AES-256-CBC-SHA
TLSv1/SSLv3:SRP-AES-256-CBC-SHA TLSv1/SSLv3:DH-DSS-AES256-GCM-SHA384
TLSv1/SSLv3:DHE-DSS-AES256-GCM-SHA384TLSv1/SSLv3:DH-RSA-AES256-GCM-SHA384
TLSv1/SSLv3:DHE-RSA-AES256-GCM-SHA384TLSv1/SSLv3:DHE-RSA-AES256-SHA256
TLSv1/SSLv3:DHE-DSS-AES256-SHA256 TLSv1/SSLv3:DH-RSA-AES256-SHA256
TLSv1/SSLv3:DH-DSS-AES256-SHA256 TLSv1/SSLv3:DHE-RSA-AES256-SHA
TLSv1/SSLv3:DHE-DSS-AES256-SHA TLSv1/SSLv3:DH-RSA-AES256-SHA
TLSv1/SSLv3:DH-DSS-AES256-SHA TLSv1/SSLv3:DHE-RSA-CAMELLIA256-SHA
TLSv1/SSLv3:DHE-DSS-CAMELLIA256-SHA TLSv1/SSLv3:DH-RSA-CAMELLIA256-SHA
TLSv1/SSLv3:DH-DSS-CAMELLIA256-SHA TLSv1/SSLv3:ECDH-RSA-AES256-GCM-SHA384
TLSv1/SSLv3:ECDH-ECDSA-AES256-GCM-SHA384TLSv1/SSLv3:ECDH-RSA-AES256-SHA384
TLSv1/SSLv3:ECDH-ECDSA-AES256-SHA384 TLSv1/SSLv3:ECDH-RSA-AES256-SHA
TLSv1/SSLv3:ECDH-ECDSA-AES256-SHA TLSv1/SSLv3:AES256-GCM-SHA384
TLSv1/SSLv3:AES256-SHA256 TLSv1/SSLv3:AES256-SHA
TLSv1/SSLv3:CAMELLIA256-SHA TLSv1/SSLv3:PSK-AES256-CBC-SHA
TLSv1/SSLv3:ECDHE-RSA-AES128-GCM-SHA256TLSv1/SSLv3:ECDHE-ECDSA-AES128-GCM-SHA256
TLSv1/SSLv3:ECDHE-RSA-AES128-SHA256 TLSv1/SSLv3:ECDHE-ECDSA-AES128-SHA256
TLSv1/SSLv3:ECDHE-RSA-AES128-SHA TLSv1/SSLv3:ECDHE-ECDSA-AES128-SHA
TLSv1/SSLv3:SRP-DSS-AES-128-CBC-SHA TLSv1/SSLv3:SRP-RSA-AES-128-CBC-SHA
TLSv1/SSLv3:SRP-AES-128-CBC-SHA TLSv1/SSLv3:DH-DSS-AES128-GCM-SHA256
TLSv1/SSLv3:DHE-DSS-AES128-GCM-SHA256TLSv1/SSLv3:DH-RSA-AES128-GCM-SHA256
TLSv1/SSLv3:DHE-RSA-AES128-GCM-SHA256TLSv1/SSLv3:DHE-RSA-AES128-SHA256
TLSv1/SSLv3:DHE-DSS-AES128-SHA256 TLSv1/SSLv3:DH-RSA-AES128-SHA256
TLSv1/SSLv3:DH-DSS-AES128-SHA256 TLSv1/SSLv3:DHE-RSA-AES128-SHA
TLSv1/SSLv3:DHE-DSS-AES128-SHA TLSv1/SSLv3:DH-RSA-AES128-SHA
TLSv1/SSLv3:DH-DSS-AES128-SHA TLSv1/SSLv3:DHE-RSA-SEED-SHA
TLSv1/SSLv3:DHE-DSS-SEED-SHA TLSv1/SSLv3:DH-RSA-SEED-SHA
TLSv1/SSLv3:DH-DSS-SEED-SHA TLSv1/SSLv3:DHE-RSA-CAMELLIA128-SHA
TLSv1/SSLv3:DHE-DSS-CAMELLIA128-SHA TLSv1/SSLv3:DH-RSA-CAMELLIA128-SHA
TLSv1/SSLv3:DH-DSS-CAMELLIA128-SHA TLSv1/SSLv3:ECDH-RSA-AES128-GCM-SHA256
TLSv1/SSLv3:ECDH-ECDSA-AES128-GCM-SHA256TLSv1/SSLv3:ECDH-RSA-AES128-SHA256
TLSv1/SSLv3:ECDH-ECDSA-AES128-SHA256 TLSv1/SSLv3:ECDH-RSA-AES128-SHA
TLSv1/SSLv3:ECDH-ECDSA-AES128-SHA TLSv1/SSLv3:AES128-GCM-SHA256
TLSv1/SSLv3:AES128-SHA256 TLSv1/SSLv3:AES128-SHA
TLSv1/SSLv3:SEED-SHA TLSv1/SSLv3:CAMELLIA128-SHA
TLSv1/SSLv3:PSK-AES128-CBC-SHA TLSv1/SSLv3:ECDHE-RSA-RC4-SHA
TLSv1/SSLv3:ECDHE-ECDSA-RC4-SHA TLSv1/SSLv3:ECDH-RSA-RC4-SHA
TLSv1/SSLv3:ECDH-ECDSA-RC4-SHA TLSv1/SSLv3:RC4-SHA
TLSv1/SSLv3:RC4-MD5 TLSv1/SSLv3:PSK-RC4-SHA
TLSv1/SSLv3:ECDHE-RSA-DES-CBC3-SHA TLSv1/SSLv3:ECDHE-ECDSA-DES-CBC3-SHA
TLSv1/SSLv3:SRP-DSS-3DES-EDE-CBC-SHA TLSv1/SSLv3:SRP-RSA-3DES-EDE-CBC-SHA
TLSv1/SSLv3:SRP-3DES-EDE-CBC-SHA TLSv1/SSLv3:EDH-RSA-DES-CBC3-SHA
TLSv1/SSLv3:EDH-DSS-DES-CBC3-SHA TLSv1/SSLv3:DH-RSA-DES-CBC3-SHA
TLSv1/SSLv3:DH-DSS-DES-CBC3-SHA TLSv1/SSLv3:ECDH-RSA-DES-CBC3-SHA
TLSv1/SSLv3:ECDH-ECDSA-DES-CBC3-SHA TLSv1/SSLv3:DES-CBC3-SHA
TLSv1/SSLv3:PSK-3DES-EDE-CBC-SHA
---
Ciphers common between both SSL end points:
ECDHE-ECDSA-AES256-GCM-SHA384 ECDHE-ECDSA-AES128-GCM-SHA256 ECDHE-RSA-AES256-GCM-SHA384
ECDHE-RSA-AES128-GCM-SHA256 DHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES128-GCM-SHA256
ECDHE-ECDSA-AES256-SHA384 ECDHE-ECDSA-AES128-SHA256 ECDHE-RSA-AES256-SHA384
ECDHE-RSA-AES128-SHA256 ECDHE-ECDSA-AES256-SHA ECDHE-ECDSA-AES128-SHA
ECDHE-RSA-AES256-SHA ECDHE-RSA-AES128-SHA AES256-GCM-SHA384
AES128-GCM-SHA256 AES256-SHA256 AES128-SHA256
AES256-SHA AES128-SHA DES-CBC3-SHA
Signature Algorithms: RSA+SHA256:RSA+SHA384:RSA+SHA1:ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA1:DSA+SHA1:RSA+SHA512:ECDSA+SHA512
Shared Signature Algorithms: RSA+SHA256:RSA+SHA384:RSA+SHA1:ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA1:DSA+SHA1:RSA+SHA512:ECDSA+SHA512
Supported Elliptic Curves: 0x001D:P-256:P-384
Shared Elliptic curves: P-256:P-384
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID:
Session-ID-ctx: 01000000
Master-Key: 0A02D62FB6658CBCCFFD590177B9675207885CC7C87C1FFA1636F55F5750B141CAA7BD84945BE6B9279B4657A8A6E23A
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1520992482
Timeout : 300 (sec)
Verify return code: 0 (ok)
---
0 items in the session cache
0 client connects (SSL_connect())
0 client renegotiates (SSL_connect())
0 client connects that finished
4 server accepts (SSL_accept())
0 server renegotiates (SSL_accept())
1 server accepts that finished
0 session cache hits
0 session cache misses
0 session cache timeouts
0 callback cache hits
0 cache full overflows (128 allowed)
---
no client certificate available
[이 글에 대해서 여러분들과 의견을 공유하고 싶습니다. 틀리거나 미흡한 부분 또는 의문 사항이 있으시면 언제든 댓글 남겨주십시오.]